SOME PHONES PROMISE PRIVACY…
CRYPTOPHONE delivers smart security!
Secure Calls & Messaging
Secure on any network including 2G GSM, 3G UMTS/W-CDMA, LTE, and Wireless LAN
Detect Location Tracking
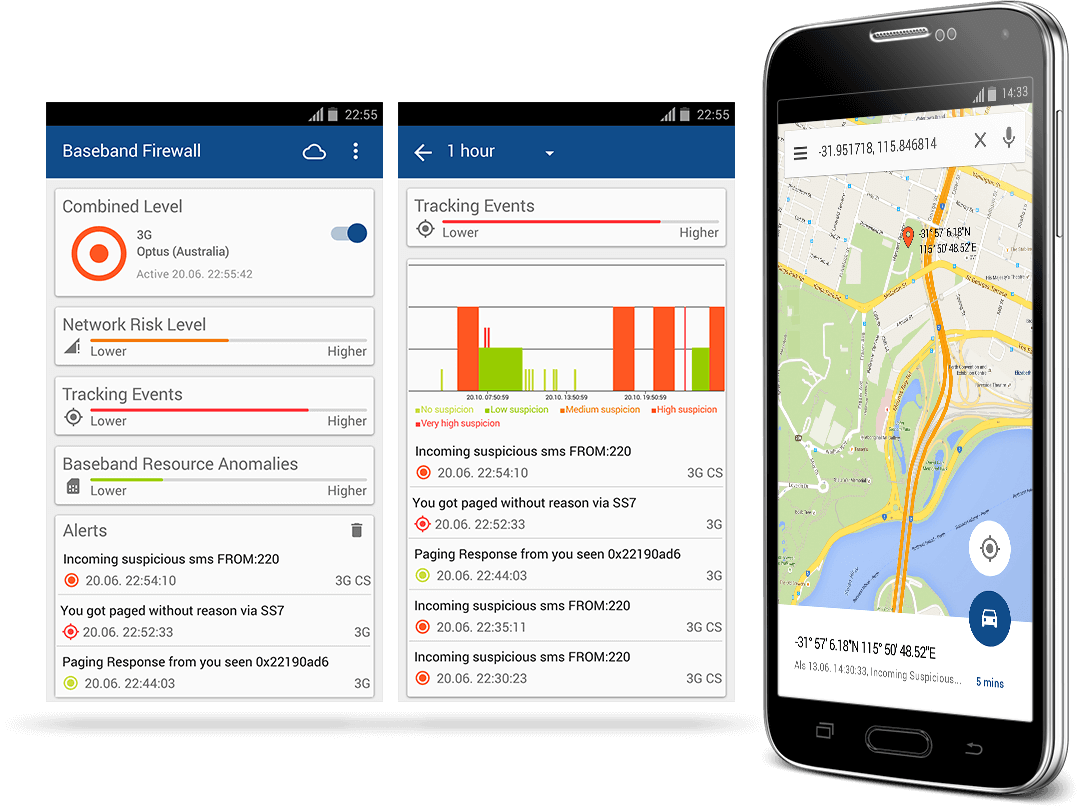
Detect IMSI Catcher activity plus tracking attempts via ‘Silent SMS’ & SS7 Paging Requests
Unique Protection Against Over-The-Air Attacks
Automatic discovery of IMSI Catchers and rogue base stations • Detection of attempts to track user location via SS7 or silent SMS
By combining GSMK’s renowned end-to-end voice and message encryption with a highly sophisticated approach towards mobile device protection, the Cryptophone 500i provides users with a hardened operating system, Baseband Firewall, and tamper-resistant hardware for true 360° mobile device security.
GOVERNMENTS, foreign intelligence services, private detectives —USE SILENT SMS & SS7 TO TRACK ANYONE THEY WANT.
WITH A CRYPTOPHONE CP 500i YOU CAN DETECT IT, ANYTIME YOU WANT!
Permission Enforcement Module
Detects application interactions with the device
Be informed about what apps really have access to
List all functions accessed by an application
Don’t be fooled by apps that want more access than you’re prepared to give
Allows you to block or spoof specific requests
Download an app in China but make it think you’re still at the hotel weeks later

Secure Storage protect your data from unauthorized access
Secure Contacts
Keep your contacts list secure
Secure Call History
The need to protect ‘when you called’ is just as important as ‘who you called’
Secure SMS folder
Keep secure messaging history and messages content secure
Secure Notes
Keep your notes content secure

Technical Specifications
SECURE IP MOBILE PHONE WITH 360° MOBILE DEVICE SECURITY
Secure Calls
Secure end-to-end encrypted voice over IP calls on any network – 2G, 3G, 4G, WLAN • Strongest andmost secure algorithms available today – AES256 and Twofish • 4096 bit Diffie-Hellman key exchange with SHA-256 hash function • Readout-hash basedkey authentication • Autonomous key generation, no pre-installed key material • Encryption keys securely and immediately erased from the device after each call
Secure Messaging
Based on the same strong encryption algorithms used for GSMK CryptoPhone voice encryption –4096 bit Diffie-Hellman initial key exchange, AES256and Twofish message encryption with 256 bit keys
Device Protection
Hardened operating system with secure boot and device runtime integrity checks
Secure Android OS built from source code with granular security management and streamlined, security-optimized components and communication stacks • Seamless secure boot chain featuring secure boot, kernel, recovery, kernel object and APK signature keys • Runtime checks of core applications and services ensure that only signed and trusted code is loaded on the device
Configurable OS security profiles
Hardware module controller and permission enforcement module control access to network, data and sensors (camera, microphone, etc.), keeping you in control of your individual security policies
Baseband Firewall 2.0
Unique protection against over-the-air attacks with constant monitoring of baseband processor activity • Baseband attack detection and initiation of counter-measures • Automatic discovery of IMSI Catchers and rogue base stations • Detection of attempts to track user location via SS7 or silent SMS
Trusted Platform Module (TPM) for platform measurement and attestation
Trusted Computing Group (TCG) TPM specifications level 2 version 1.2, revision 116 • Active shield and environmental sensors • Memory Protection Unit (MPU) • Hardware and software protection against fault injection
Verifiable Source Code
GSMK CryptoPhones are the only secure mobile phones on the market with source code available for independent security assessments. This permits individual source code audits in accordance with national and international verification and certification standards designed to verify device integrity mechanisms, correct implementation of all encryption algorithms, and the absence of backdoors
Encrypted Storage
Encrypted storage system for contacts, messages,and notes with smart folders protects data at rest against unauthorized access
Take control of your privacy today
Secure calls and messages on any network – GSM, 3G, 4G, LTE, WLAN
Specifications
Compatibility
Fully compatible with all GSMK CryptoPhone IP devices (mobile, landline, satellite) and with GSMK CryptoPhone IP PBX Gateway.
Also you can use it as usual GSM mobile phone.
Processor
Quad–core Krait CPU 2.3GHz
Graphics accelerator
QDSP
Radio
GSM/GPRS/EDGE (850/900/1800/1900 MHz)
UMTS/HSDPA+ (B1, B2, B4, B5, B8)
LTE advanced (3GPP, FDD, IMS, VoLTE, Carrier Aggregation, B2, B3, B4 , B5, B7, B13, B14, B17, B20)
Connectivity
Integrated microUSB 3.0/power connector • 3,5 mm stereo audio jack • microSD memory card slot – microSDHC • transFlash, microSDXC compatible • IEEE 802.11 a/b/g/n/ac Wireless LAN.
Display
5.1-inch sunlight-readable touch sensitive HD Super AMOLED screen @ 1920 x 1080 pixels, 24 bit color depth • Corning Gorilla glass 3.
Digital Camera
Main camera with 15,9 megapixels resolution (5.312 x 2.988) with auto focus, built-in flash and integrated 1D and 2D bar code decoding • front camera with 2,1 megapixels resolution (1.920 x 1.080) • cameras can be completely disabled by hardware module controller.
Dimensions & Weight
142 x 72,5 x 8,1 mm/ 5,6 x 2,9 x 0,3 inches • 145 g/ 5,1 oz. incl. battery • integrated antenna.
