General Questions
CryptoPhones are cellular, desktop or satellite phones that provide security against anyone listening in on your calls and mobile messages. To set up a secure call or communicate by encrypted SMS/Internet messages, both parties need to use a CryptoPhone.

We designed GSMK CryptoPhones to offer security against anyone who tries to listen into your calls or intercept your SMS, both inside the telephone network and on the air. GSMK CryptoPhones provide end-to-end security so the call or SMS is fully encrypted all the way between the two CryptoPhones involved in a call. CryptoPhone Secure Storage protects data on the phone from unauthorized access and smart BaseBand FireWall protects against over-the-air attack.
Today’s complex telephone systems make it impossible to predict what path a communication link takes inside the network. Calls and messages are routinely transported over unencrypted directional microwave radio links that are subject to easy interception with simple equipment. In order to save costs, calls are frequently routed through networks or operators that might have dubious security standards. Your whole business confidentiality might get compromised by a single corrupt phone company employee. There exist devices known as “IMSI-Catchers” which allow anyone to listen into mobile phone calls. IMSI-Catchers are readily available on the market and are being used with increasing frequency. All these threats can be eliminated by using the CryptoPhone.

When you are operating with sensitive information that could possibly cause danger or damage to you or your clients if compromised, a CryptoPhone is right for you. If you ever have talked on the phone and thought “let’s hope that this call has not been intercepted by someone”, the CryptoPhone is right for you. If you have ever talked about a transaction worth a million Euros or more on the phone, the CryptoPhone is also right for you.
Typical customers are corporate executives, lawyers, accountants, bankers, mergers & acquisition specialists, consultants (management, tax, security), journalists, law enforcement officers, government organizations, NGOs, private investigators and other people who simply prefer to communicate in private.

Covering the full spectrum of voice encryption, secure messaging, and mobile device security, GSMK CryptoPhones offer true 360-degree protection and the best cryptographic security available on the market.
GSMK CryptoPhones are very easy to use.
The source code of the firmware is published, meaning it is under constant review by experts for security.
GSMK CryptoPhones have been developed without any government interference and do not provide any third party access to the encrypted communication or key material.
Our products are also affordable, so that communications security does not have to be a luxury. GSMK CryptoPhone secure mobile phones are based on standard hardware, which allows you to buy accessories at normal market prices.
The team that designed and produces GSMK CryptoPhones has spent the better part of fifteen years thinking about it. During this time, we have brainstormed with the top security people around the globe on how to do it right. One thing was clear from the start: The computer code behind the system must be available to the cryptographic/academic community (and to the public at large) to allow flaws and backdoors to be discovered and fixed as fast as possible. There is no other secure cellular, landline, or satellite phone on the market that offers this extremely important feature.
Questions about the Interception of GSM Calls
Not all GSM providers can afford to have ‘land lines’ connecting their antennas on the street with the switching station and the rest of the telephone network. If you have ever seen a GSM base station antenna mast, you might notice that some of them have little round ‘dishes’, or ‘beamers’ at the side of it. These are the directional antennas for the microwave links that provide the connection to the rest of the network.
Over these links, all calls made in the area are transmitted to a point where they are fed into landlines. These links are very vulnerable, because no encryption is used on most of them. An interceptor can tap into the radio signal, and listen in to many call simultaneously. Commercial equipment for this kind of interception is available on the market at moderate prices.
Interception of microwave links is commonly used when targeting a fixed facility, like a competitor’s office building. Attacks on corporations can be quite effective with this method, since there is often a company standard for the network operator of choice, so just one intercepted microwave link could yield all mobile phone calls taking place in the facility.
Nothing more is required than a very small rooftop antenna in the path or vicinity of the microwave link, a wideband receiver and the appropriate channel demultiplexing and recording equipment. Embassies of foreign countries are known to use microwave link interception from their various premises to stay secretly informed on what is happening in their host country. Embassies are usually located near the business and government centers, so this kind of interception has the potential to yield substantial information. Since the antenna radiation patterns of the microwave links contain so called sidelobes, receiption of their signals with sensitive receivers is also possible outside the straight line of the link.
The NSA (National Security Agency, the electronic surveillance intelligence agency of the USA) is also known to have satellite-based microwave link interception capabilities. Since the directional microwave beam does not stop at the receiving antenna, but travels further on in the original direction, it can be intercepted from space with a satellite placed at the appropriate position.
GSMK CryptoPhones protect against this kind of interception.
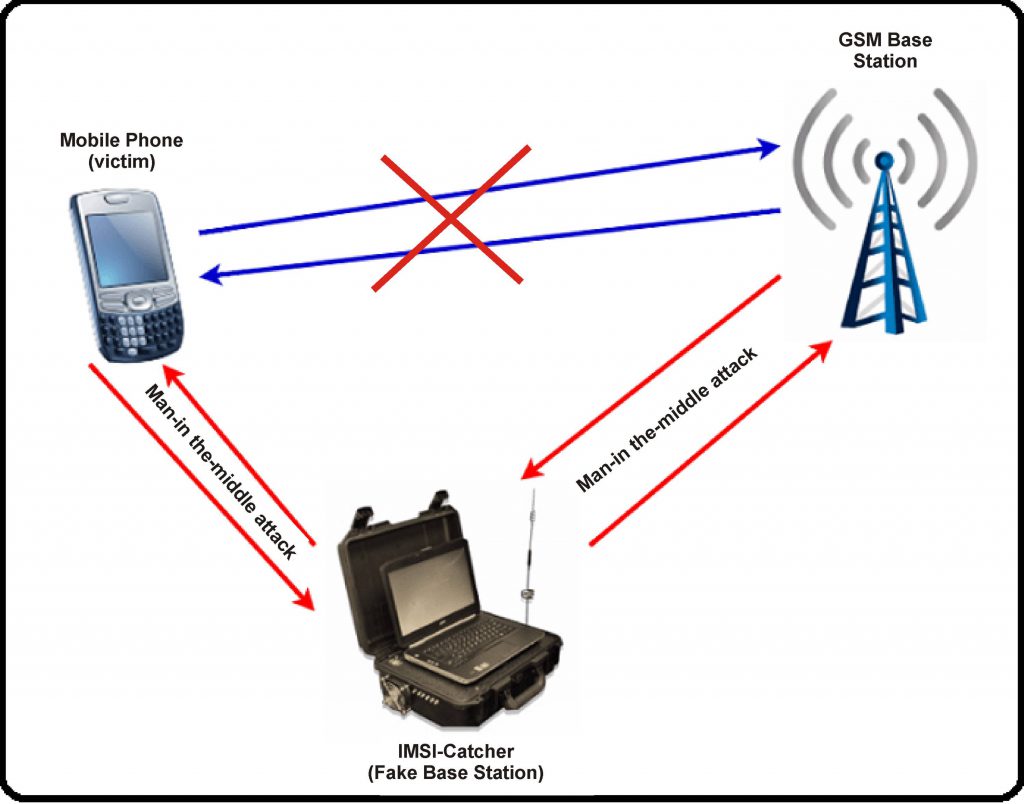
An IMSI-catcher is a device that can be used to determine the electronic identities of all phones in its vicinity. Most IMSI-Catchers also come with the ability to listen into calls directly. The electronic identity consists of the so called International Mobile Subscriber Identity (IMSI), which is associated with your SIM card and the International Mobile Equipment Identifier (IMEI), which is the serial number of your phone. With the IMSI your calls can be easily identified at any point in the telephone network and targeted for interception and traffic analysis. An IMSI-catcher is frequently used if the attacker does not know the telephone number of the victim or wants to illegally intercept calls.
The IMSI-catcher performs a so called man-in-the-middle-attack, putting itself between you and the network. It is essentially a small GSM base station that forces your phone to use it instead of the real network, determines your IMSI, and can then be used to disable or degrade the GSM encryption mode while transmitting your call on to the legitimate network. This mode of operation allows the attacker to directly listen into your calls. He can also disable your phone service and intercept or fake SMS messages to and from your phone.
At this moment we know of many different companies producing IMSI-catcher devices, and the list is growing rapidly. For a company manufacturing GSM test equipment, developing IMSI-catchers is a trivial task. Examples of publicly available IMSI-catcher equipment also include regular laptops that are connected to a small portable ‘femtocell’ base station and running publicly available GSM network simulation software.
Even when IMSI-catchers are used by legitimate law-enforcement agencies, they frequently affect a high number of calls that are not their target. The resulting number of unintended intercepts is called “by-catch” and is frequently used for all sorts investigations, especially popular with tax authorities in some countries.
GSMK CryptoPhones protect against the interception of the call content with an IMSI catcher.

Telecommunications interception has developed into a major industry in the last decades. Intelligence agencies of all countries routinely try to intercept calls that might yield them political, economic or military information. Several large intelligence agencies, like the NSA together with the british GCHQ run global surveillance networks that work like a big hoover, sucking in huge amounts of telecommunication with a vast worldwide system of antennas, special satellites, undersea and land cable taps, backdoors in switching stations and any other means available. The biggest computer capacities on earth are subsequently used to evaluate the calls, SMS, emails and faxes based on complex sets of criteria, forwarding the ones matching specific criteria to human analysts and database storage.
Today even small countries run their own sprawling listening and monitoring stations. They also try to get access to the big players’ interception capabilities by trading them the access to bases, facilities and interception results. The targets of these listening networks are not very specific. More and more of the capabilities are being used for economic espionage, but of course also to further the more or less noble intentions of the nation states that paid for them. If you think that these systems are only used in rare cases where national security is at stake, you are wrong.
Telecommunications surveillance has become a fairly routine method for intelligence agencies and governments to stay informed on anyone who is even remotely capable of interfering with political or business interests. A set of agreements between intelligence agencies makes sure that the local provisions that hinder them to listen to their own people are not of any consequence. If the NSA wants to listen to a US citizen it asks the British GCHQ to do the intercept and then put the results into a shared database used by both agencies.
Other potential listeners work at the various phone companies. All network operators have listening capabilities for the purpose of “network trouble shooting” and “fraud detection”. These capabilities have been used routinely by corrupt phone company employees for their personal gain, selling call data and contents to criminal elements and industry spooks.
Private investigators also routinely and illegally try to get access to calls by a variety of means, for purposes of industrial espionage, business intelligence and economic warfare between competing companies. Big corporations have often have their own capabilities for telecommunications interception, especially in high-risk fields such as oil, minerals, fishery, mergers & aquisition and investment banking, to name just a few.
Law enforcement agencies have in the last years acquired an ever-rising set of capabilities, with ever-shrinking restrictions on their use. In almost all cases of even legitimate lawful interception a significant number of innocent people also got caught in the dragnet of surveillance (so called “by-catch”). Even if state laws would have required the innocent people to be notified, this often does not take place. Legal oversight in most countries is poor at best and routinely circumvented using various pretexts. Trusting that law enforcement agencies use interception carefully and only under strictly warranted circumstances is no longer justified. The number of reports about abusive and excessive use of interception without proper cause and even for minor infractions is raising substantially.
Intercept systems for law enforcement are often designed in such a way as to make it impossible to perform independent reviews on the usage of the surveillance devices. Even simple statistics on the number of interceptions are routinely held secret. The interception technology for law enforcement is also frequently sold by rather dubious companies. Almost all of these manufacturers have strong ties to foreign intelligence agencies. Practically all lawful interception products contain remote maintenance facilities, so it must be assumed that they contain backdoors. Such a backdoor is of course an interesting bargaining chip on the international intelligence bazaar.
“Lawful interception” also means a very different thing from country to country. In a dictatorship or some other less then democratic state, it is frequently “lawful” to intercept anyone at will. The technology for interception is available on the open market and is widely deployed even in the poorest areas of the world. It would be naive to assume that the term “lawful interception” somehow automatically meant that the interception is performed under even the most basic legal oversight.

First of all, the encryption in GSM is only used to protect the call while it is in the air between the GSM base station and the phone. During its entire route through the telephone network (which may again include wireless links) the call is not protected by encryption anymore.
Secondly, it has been shown over and over again that standard GSM encryption is not good enough to protect your calls. GSM providers claim there is no problem, because a proprietary set of encryption algorithms named A5 is used. They tend to forget to tell you that most varieties of A5 in current use are weak and that experts have proven time and time again that this encryption is by far not sufficient against a determined listener.
There a four modes of A5 encryption currently in use:
- A5/0 means no encryption at all. Even in regular network operation this mode is used from time to time because of technical difficulties or outside interference. In certain countries network operators have been forced to switch back to A5/0 in times of “crisises”. Being between the GSM network and the phone the IMSI-Catcher can also direct telephones to use A5/0. Some network operators switch to A5/0 to save a little bit of bandwith in times of high network usage. The GSM specification requires phones to indicate to the user when crypto is set to A5/0, but there are several phones known not to comply with this requirement.
- A5/1 is the encryption mode used in Europe and other western countries. It is a bit stronger than A5/2, but can still be broken with moderate resources that are available to any private attacker with sufficient determination.
- A5/2 is the encryption mode used in Australia and several other countries worldwide. It has been broken time and again in realtime, on a standard personal computer. See our list of academic papers detailing the vulnerabilities.
- A5/3 is the algorithm that will be introduced for the next generation of networks and phones. It is claimed to be stronger then A5/2, but A5/3, too, has been shown to be broken by leading academic researchers. Plus, of course, even with A5/3 you are still vulnerable to man-in-the-middle-attacks like with an IMSI-catcher and it still your call is encrypted only in the air, not on the telco network. Over the past few years we have seen mathematical breakthroughs reducing the amount of computer-time needed to decode GSM calls. Since the cryptographic algorithms in GSM are currently the most widely used crypto system on earth, it is a very tempting target for cryptographers and mathematicians. GSMK CryptoPhones protect against this kind of interception.
Questions about the Cryptophone Technology
All CryptoPhone calls are encrypted with 256-bit keys using AES and Twofish as counter mode stream ciphers. For SMS the algorithms are used in CCM-mode. Using both AES and Twofish results in much stronger encryption than using only one algorithm. For the highly unlikely case that a weakness is discovered in one of the algorithms, the use of the second algorithm provides still a sufficient margin of security. The use of the two very strong algorithms is a unique feature of the CryptoPhone. The key used is generated using a 4096-bit Diffie-Hellman shared secret exchange. For CryptoPhone calls a new key exchange is run for every call. For SMS the result of an initial key exchange is stored in the Secure Storage on the phone and used by means of a hash-chain.
The crypto block diagram is shown below: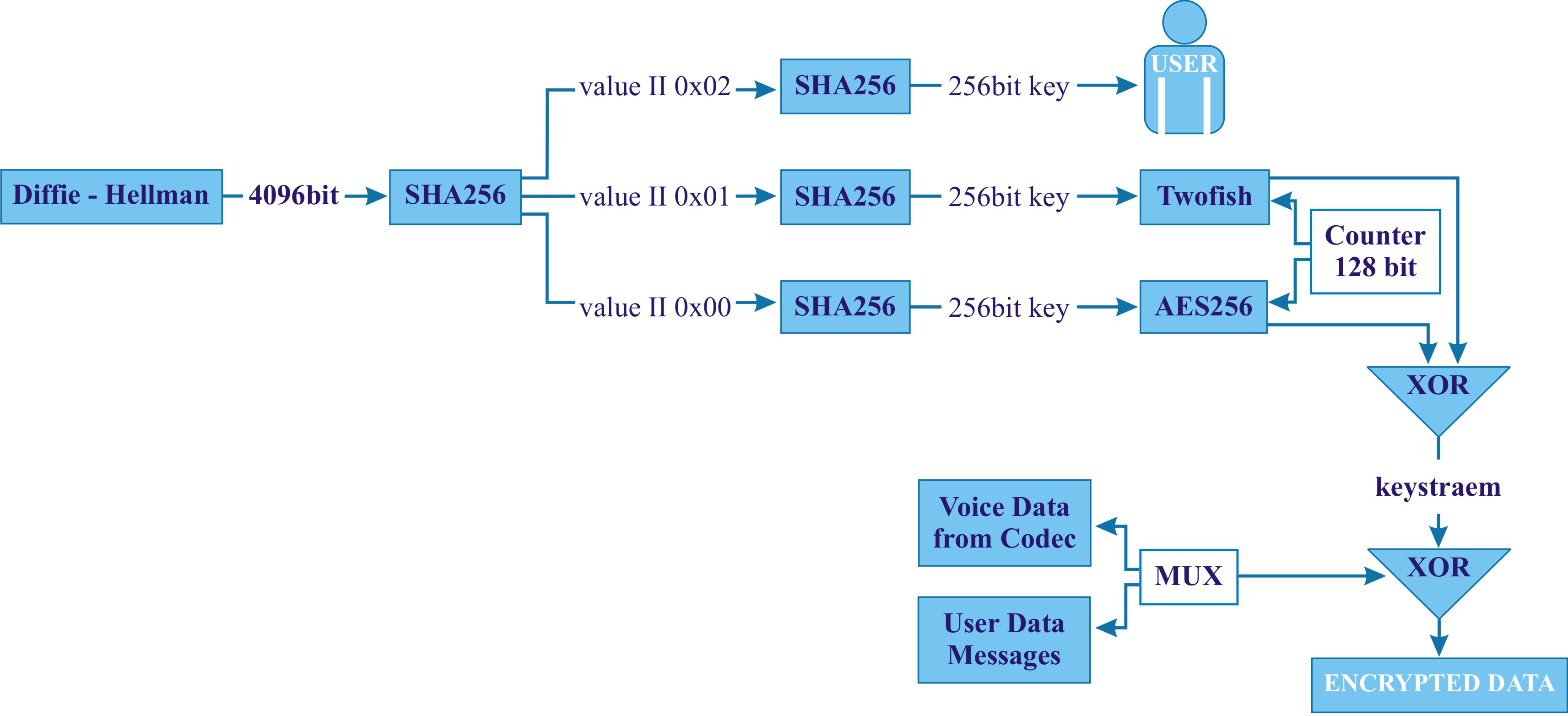
The basic design of a secure GSM phone is to take the voice from the microphone, digitize it and run it through a compression algorithm, before encrypting it and sending it via a GSM data call to the other party. The compression algorithm is also called a codec and does with voice what mp3 does with music – making sure it takes up less data.
CryptoPhones use ACELP voice codec which provides significantly improved sound quality while reducing the necessary bandwidth usage. The ACELP variant has been specifically optimized for an output bandwidth of only 4 kbit/s, so the complete CryptoPhone stream including all overhead data requires less then 4,8 kbit/s.
The speech and sound quality you can expect is comparable to international phone calls. You should note that the overall speech quality depends on the GSM signal quality, so degradation does happen in low coverage areas. While in unencrypted GSM the sound quality gets bad and you would experience dropouts as the phone moves out of coverage, with the CryptoPhone under the same circumstances the call delay can increase. Simple indicators on the CryptoPhone show GSM signal coverage and call quality / delay.
All calls made with mobile CryptoPhone are subject to a certain delay in the call, as if your call is routed over a satellite link. Most of the call delay originates from the way GSM networks handle the data calls. The CryptoPhone must use the GSM data call instead of the normal voice call mode to ensure a transparent communications channel between the two CryptoPhones. Because the delay is a side-effect of all GSM data calls there is nothing we can do about it. All available GSM encryption products on the market suffer equally from this delay. The CryptoPhone itself introduces comparatively little delay from the voice encoding and encryption. By consequence, GSMK CryptoPhone secure fixed-line phones are not subject to any such mobile network limitations.
CryptoPhone mobile phones run on top of a heavily modified and stripped-down Android OS. Android OS provides an affordable and well-researched platform that offers ample performance for the speech encoding and crypto functions. Android OS based system was chosen as the first CryptoPhone platform because it was the only sufficiently fast device allowed us to do software integrity protection in ROM and the stripping of unnecessary functions.
We are aware that there are risks associated with using any Android OS platform and we have taken a number of extensive measures to mitigate these risks as best as we could. We removed applications, communication stacks and system parts that are unnecessary for the CryptoPhone’s operation and which may cause potential security problems. Since we introduced our operating system hardening in 2008, for every attack that was published against Android since then we could show that we had already identified the threat and disabled the affected components years before in CryptoPhones. While this is no guarantee for the future, we have at least a provable continuous track record in respect to systematically securing mobile devices, which is much more than our competition has to show.
Most important for you as a user is that you should not install third party software on the CryptoPhone to prevent software based attacks on the firmware integrity. Protection against trojaned software that is intentionally installed by the user is nearly impossible, so it is your responsibility as a user to prevent that risk by not installing untrusted software on your device. The CryptoPhone firmware update mechanism is cryptographically secured.
The diagram below provides a schematic overview of the software architecture of GSMK CryptoPhones for your reference: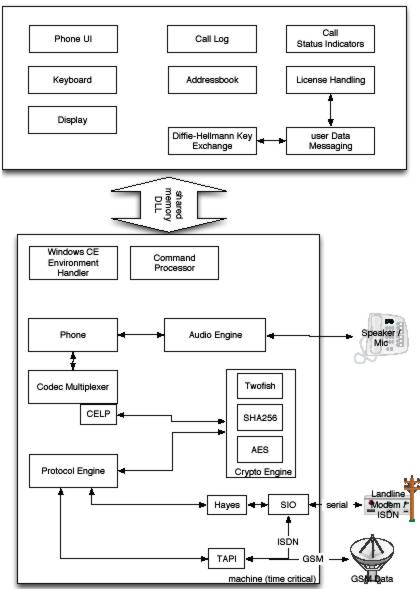
GSMK CryptoPhone mobile phone run on top of a heavily modified and stripped-down Android operating system. Android provides an affordable and well researched platform that offered sufficient performance for the speech encoding and crypto functions. ANdroid OS based system was chosen as the platform for CryptoPhone because it was the only sufficiently fast device allowed us to do software integrity protection in ROM and the stripping of unnecessary functions.
We are aware that there are risks associated with using any Android platform and we have taken a number of extensive measures to mitigate these risks as best as we could. We removed applications, communication stacks and system parts that are unnecessary for the CryptoPhone’s operation and which may cause potential security problems. Since we introduced our operating system hardening, for every attack that was published against Android OS we could show that we had already identified the threat and disabled the affected components years before in CryptoPhones. While this is no guarantee for the future, we have at least a provable continuous track record in respect to systematically securing mobile devices, which is much more than our competition has to show.
Most important for you as a user is that you should not install third party software on the CryptoPhone to prevent software based attacks on the firmware integrity. Protection against trojan software that is intentionally installed by the user is nearly impossible, so it is your responsibility as a user to prevent that risk. The CryptoPhone firmware update mechanism is cryptographically secured.
Questions about Published Source
The ‘source code’ is the blueprint of how the crypto-phone operates, and computer programmers can read this code. Cryptography/security is a fine art, and one simple error can introduce a serious flaw into the product. Customers of communication security devices have always had to fear not only programming errors, but also so called “back doors”. Such a back door would allow certain people to listen into encrypted calls at all times, for instance by revealing (part of) the cryptographic key during the call.
Introducing a back door into a crypto system does not even require active cooperation of the manufacturer of the equipment. All it takes is one bribed programmer to compromise an entire product.
We prevent this by allowing anyone to review our source code. And even if you do not understand the source code yourself you may find some comfort in the knowing there is a large academic community that likes a challenge, and will try to tackle our product. So any back door or programming error can (and will!) be found by eager students or security enthusiasts. Of course we tried our very best to write the code as well as we know how to. On top of this we have asked some of the world’s leading security consultants to look at critical parts of it. The conclusions of these ongoing evaluations are publicly accessible. So in theory you would not need to trust us at all, because you could verify everything yourself. This public review process is also the only reliable method for us to make sure that we are the only one paying our developers ;-).
We can only assume the other vendors have something to hide. They might be afraid of competition and want to protect so called “trade secrets”. The nice thing about our product is that we have no (trade) secrets, and invite everyone to make interoperable products based on the published protocol. We believe in standards that are open for anybody to join – as long as they go and implement their own product and do not steal from our published source.
Some manufacturers of cryptographic equipment, that are also currently in the business of selling secure mobile phones, have a track record of hidden cooperation with intelligence agencies and interested private parties. Some of them are not even using publicly scrutinized and standardized crypto algorithms (like the Diffie-Hellman, SHA256, AES and Twofish that we use), but “proprietary” encryption methods that are not available for public evaluation. Several “proprietary” crypto-algorithms that were not subject to public review have been shown to be easily breakable in the past, like the COMP128 algorithm that is in use in many GSM networks for authentication, so the “proprietary crypto” approach has to be regarded as very risky. The CryptoPhone contains only algorithms that are published, well known and thoroughly reviewed by the academic cryptography community.
We take a number of steps to ensure that you really get the correct firmware. The source code repository for the CryptoPhone is held at a computer that only our trusted developers can make changes to, and that is secured against physical access. If you plan to purchase a larger batch of CryptoPhones, we can arrange for a dedicated procedure that enables you to supervise every production step from the source code you reviewed to the the binary that goes into your batch of phones.
Please send us an e-mail to darseta@darseta.lt with a detailed full description if possible including source snippets and your contact coordinates (PGP encrypted mail preferred, see Contacts page for key). If you prefer to stay anonymous we are fine with that, but please make very sure we can reach you via an e-mail account of your choice.
We will contact you immediately to acknowledge that we received your message and begin checking into the problem at once. You will get a dedicated contact person assigned for the verification process, to make sure there are no glitches in the communication with you. We will in no way interfere with your right to be named as the discoverer of the problem and acknowledge your findings on the security section of our website upon publication. However we kindly ask you to hold publication until we provided a security update to our users, to make sure they are not left out in the cold with a security problem. Our goal is to have a maximum turnaround period of 30 days between reproduction of the problem and publication, depending on severity and impact. We will inform you on the progress of our fixing efforts on a regular and timely basis.
Finders of serious problems will be awarded the CryptoPhone Award for Extreme Cleverness and a present (guess what…).
Questions about Purchase and Usage of Cryptophone Products
The best way is to order your CryptoPhone from your local Authorized GSMK CryptoPhone Reseller – UAB “Darseta”.
Some manufacturers of cryptographic equipment, that are also currently in the business of selling secure mobile phones, have a track record of hidden cooperation with intelligence agencies and interested private parties. Some of them are not even using publicly scrutinized and standardized crypto algorithms (like the Diffie-Hellman, SHA256, AES and Twofish that we use), but “proprietary” encryption methods that are not available for public evaluation. Several “proprietary” crypto-algorithms that were not subject to public review have been shown to be easily breakable in the past, like the COMP128 algorithm that is in use in many GSM networks for authentication, so the “proprietary crypto” approach has to be regarded as very risky. The CryptoPhone contains only algorithms that are published, well known and thoroughly reviewed by the academic cryptography community.
No. All sales are final. Each GSMK CryptoPhone is a Communication Security (COMSEC) device that is configured, packaged and security sealed individually for you and is therefore not subject to the two-week return policy for consumer electronics ordered online. The reason is that once a phone has been in the hands of a customer, we can not sell it to another customer, because there is no economic way to check for all the possible modifications and tampering that could have affected the security of the device. Think of it like the no-returns policy that applies to tailored suits and other similar products. On questions of warranty, see below.
We use a variety of high-security seals and procedures to help make sure the device arrives at your doorstep as we shipped it. If you want to verify the integrity of the package, please follow the instructions that you can obtain after ordering. Special verification procedures basically require you to send us an e-mail upon reception of the package, but before opening it. You will then immediately receive an e-mail from us with the types and serial-numbers of seals that we used to secure your package as well as pictures of where and how the seals were placed. We may at our discretion also include information on additional hidden security markers used for your package.
We regularly perform anonymous test purchases of the CryptoPhone GSM to verify the integrity of the entire delivery chain. All orders are shipped directly from our secure production facilities without unnecessary delays. If you are ordering via one of our resellers, resellers are required to notify you immediately when the shipment arrives, hand you the fully sealed package and envelope with all seals intact and store both in a secure place until you pick up the CryptoPhone.
All mobile, satellite and desktop CryptoPhones come with a one-year manufacturer warranty. In the unlikely event that your CryptoPhone needs warranty repairs, please contact us first at darseta@darseta.lt, so we can inform you about the detailed warranty and shipment procedure. Please be aware that certain fees for shipment and security sealing might apply. You must obtain a Return Merchandise Authorization (RMA) number before returning any equipment to us. Return shipments without a confirmed RMA number will be ignored. Please note that the integrated battery of the CryptoPhone is subject to wear and tear and not covered by the warranty.
We offer firmware updates for the CryptoPhone, e.g. when additional features become available for your device. Updates generally fall into two categories: security updates and feature updates. Security updates will be made available in the case a security problem has been discovered. Security upgrades are free for download as long as the main firmware version they apply to is supported. Feature upgrades enhance the functionality of the CryptoPhone, and may be sold or offered for free download.
We will inform you by phone or by email about available updates. You will only have to push the button “Update” in Your device and it automatically will connect to GSMk CryptoPhone servers and will download digitaly signed updates.
