General Questions

Over the past two decades, telecommunications interception has developed into a major industry. Intelligence agencies and private organizations in all countries routinely intercept calls that may yield sensitive political, military or economic information.
The use of wiretapping has become so widespread, simple and uncontrolled that you must assume that records of your private calls and SMS end up in the wrong hands. Equipment for wireless interception of mobile phone calls and messages has become available at such low prices that it is deployed frequently even in comparatively small business conflicts. So using encryption to protect your privacy is the prudent choice.
But protecting your information with strong and trustworthy encryption has become difficult. “Proprietary” or “secret” algorithms of dubious quality, and encryption that is too weak to protect against modern computing power are commonplace in the telecommunications market. These weaknesses are masked by marketing efforts, suggesting that you need to rely on “the secrecy of the algorithm” or “government classification” – certified by the same intelligence agencies that are actually in charge of telecommunications interception.
Now there is a solution that you can trust, because it can be verified by you or by your experts. GSMK CryptoPhones, the only secure phones that come with full source code available for independent review, are available now. Finally, you can perform an independent assessment to ensure that there is no weak encryption and no backdoors in the device you entrust your telecommunications security to. You don’t have to believe us when we say it is secure – you can verify that claim yourself.
GSMK CryptoPhones are no black-box-devices with scarce technical information, like other products in the market. We will give you all the details of their inner workings – even before you buy. GSMK CryptoPhones enable you to put the trust where it belongs – in a trustworthy, open and scientific verification process.
GSMK CryptoPhone technology is based on well-researched algorithms for both encryption and voice processing: The strongest encryption available combined with key lengths that provide peace of mind today and in the future. GSMK CryptoPhones encrypt your calls with the two algorithms that are regarded strongest by the cryptographic community – AES256 and Twofish.
GSM Insecurity

The standard encryption algorithm that is supposed to protect GSM mobile telephone calls from eavesdropping has long been known to be weak. Today, the technology to crack GSM’s standard encryption algorithm is accessible even to amateurs at moderate cost. Recent public demonstrations of practical low-cost attacks on GSM’s standard A5/1 encryption algorithm have underlined just how vulnerable mobile phone calls have become.
While the cryptopgraphic weakness of the most widely used GSM algorithm A5/1 has been known for quite some time, in the year 2009 the technology to exploit the weakness has leapfrogged.
Using so called Rainbow Tables – a technique to precompute large parts of the calculations needed to actually break the algorithm – and the massively increased computing power of high-end graphic cards, the technology to listen in into GSM calls has actually become available to interested amateurs.
The Rainbow Tables can be acquired from the Internet, the necessary software-defined radio wideband receiver can be procured commercially for only a few thousand Euro. The decoding software is available as open source and is steadily improving.
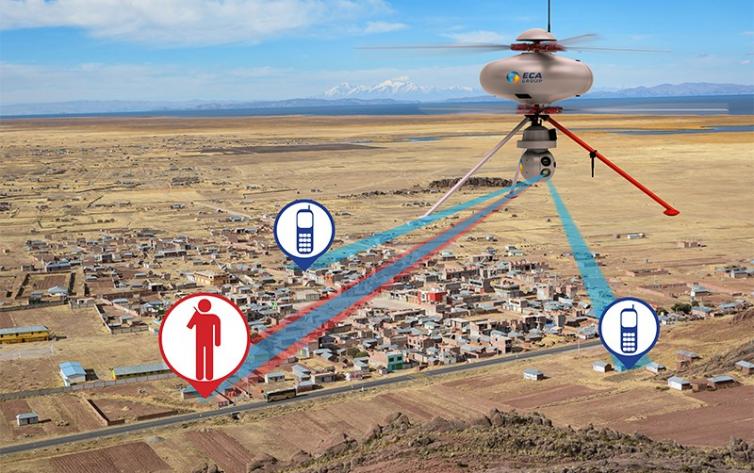
Passive GSM interception systems allow an attacker to eavesdrop on mobile telephone calls using only passive methods, i.e. equipment that only receives, but does not transmit and that is thus undetectable for the victim. Undetectable and highly portable, passive interception systems are used either for intercepting the radio link between a mobile phone and a base station, or between a base station and other network components.
A wide range of passive interception devices is available for governmental as well as private entities. Due to the non-detectability of the devices, although the usage is forbidden, the number of devices for passive interception can hardly be underestimated. The availabiliy of software-components for normal radio scanners to intercept GSM communication has already begun. With continuing downward trends in cost, passive GSM interception equipment has become very accessible even for attackers with very modest financial and technical resources.
GSMK CryptoPhones protect against the interception of call contents with passive GSM interception systems.
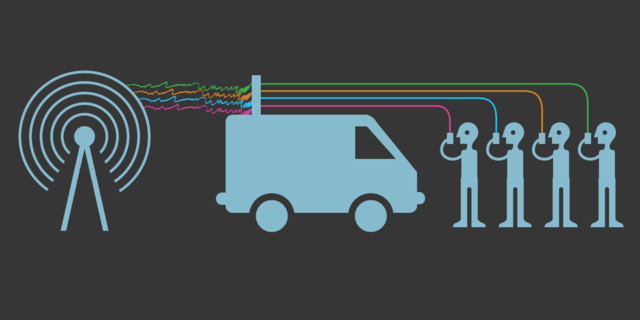
Active GSM interception systems allow an attacker to actively interfere in communications between mobile phones and base stations by means of a so-called IMSI-catcher, in essence a transmitter and receiver that simulates the functionality of a GSM base station. Recent attack methods involve spoofing so-called femtocells to feign that you are the user’s mobile network provider, while in fact you are taking over his network traffic.
An IMSI-catcher is a device that can be used to determine the electronic identities of all phones in its vicinity. Most IMSI-Catchers also come with the ability to listen into calls directly. The electronic identity consists of the so called International Mobile Subscriber Identity (IMSI), which is associated with your SIM card and the International Mobile Equipment Identifier (IMEI), which is the serial number of your phone. With the IMSI your calls can be easily identified at any point in the telephone network and targeted for interception and traffic analysis. A IMSI-catcher is frequently used if the attacker does not know the telephone number of the victim or wants to illegally intercept calls.
The IMSI-catcher performs a so called man-in-the-middle-attack, putting itself between you and the network. It is essentially a small GSM base station that forces your phone to use it instead of the real network, determines your IMSI, and can then be used to disable or degrade the GSM encryption mode while transmitting your call on to the legitimate network. This mode of operation allows the attacker to directly listen into your calls. He can also disable your phone service and intercept or fake SMS messages to and from your phone.
At this moment we know of at many different companies producing IMSI-catcher devices, and the list is growing rapidly. For a company manufacturing GSM test equipment, developing IMSI-catchers is a trivial task. See our link section for examples of publicly available IMSI-catcher equipment.
Even when IMSI-catchers are used by legitimate law-enforcement agencies, they frequently affect a high number of calls that are not their target. The resulting number of unintended intercepts is called “by-catch” and is frequently used for all sorts investigations, especially popular with tax authorities in some countries.
GSMK CryptoPhones protect against the interception call contents with an IMSI catcher.
CryptoPhone technolog
The basic design of a secure GSM phone is to take the voice from the microphone, digitize it and run it through a compression algorithm, before encrypting it and sending it via a GSM data call to the other party. The compression algorithm is also called a codec and does with voice what mp3 does with music – making sure it takes up less data.
CryptoPhones use ACELP voice codec, which provides significantly improved sound quality while reducing the necessary bandwidth usage. The ACELP variant has been specifically optimized for an output bandwidth of only 4 kbit/s, so the complete CryptoPhone stream including all overhead data requires less than 4,8 kbit/s.
The speech and sound quality you can expect is comparable to international phone calls. You should note that the overall speech quality depends on the GSM signal quality, so degradation does happen in low coverage areas. While in unencrypted GSM the sound quality gets bad and you would experience dropouts as the phone moves out of coverage, with the CryptoPhone under the same circumstances the call delay would increase. Simple indicators on the CryptoPhone show GSM signal coverage and call quality/delay.
All calls made with the CryptoPhone are subject to a certain delay in the call, as if your call is routed over a satellite link. Most of the call delay originates from the way GSM networks handle the data calls. The CryptoPhone must use the GSM data call instead of the normal voice call mode to ensure a transparent communications channel between the two CryptoPhones. Because the delay is a side-effect of all GSM data calls there is nothing we can do about it. All available GSM encryption products on the market suffer equally from this delay. The CryptoPhone itself introduces comparatively little delay from the voice encoding and encryption.

GSMK CryptoPhones IP devices support uses any form of wireless IP (internet protocol) network available. With CryptoPhone IP devices you can connect via GPRS, EDGE, 3G, LTE, WiFi or satellite devices that provide IP networking.
When you are traveling, you can plug in a data-enabled local SIM card and can still be reached on your CryptoPhone IP number.
GSMK CryptoPhone technology is based on published and well researched algorithms for both encryption and voice processing. All GSMK CryptoPhones use the same encryption engine with very long keys, resulting in products that provide peace of mind today and in the future.
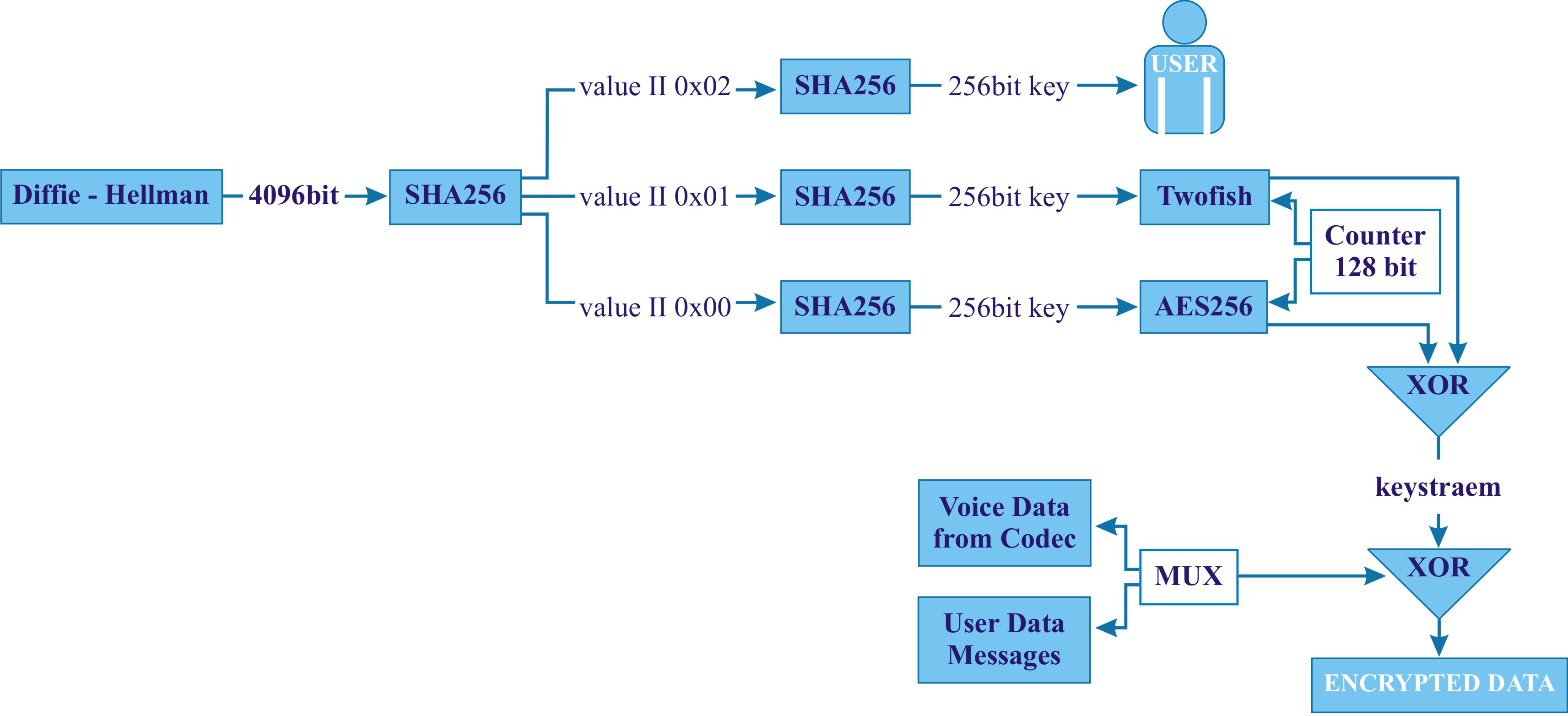
All calls are encrypted with 256-bit keys using AES256 and Twofish running as counter mode stream ciphers. For SMS the algorithms are used in CCM-mode. Using both AES256 and Twofish provides a much stronger design than using only one algorithm. For the highly unlikely case that a weakness is discovered in one of the algorithms, the use of the second algorithm provides an additional “safety net” and results in a higher security margin. The use of these two very strong algorithms is a unique feature of GSMK CryptoPhones that provide a “fall back” inside the crypto-system design. The design goal was to provide not only “tactical security” that lasts for a few months or years, but to design for security against future developments in cryptanalysis in the next decades.
The key used for each call is generated using a 4096-bit Diffie-Hellman shared secret exchange, hashing the resulting 4096 bits to the 256 bit session key by means of SHA256. To prevent man-in-the-middle attacks, a six-letter hash is generated from the Diffie-Hellman result and displayed to the user. The user then reads three letters over the encrypted line to the communication partner and verifies the three letters the communication partner reads to him. Verification of the hash ensures that both parties use the same key and that no man-in-the-middle attack was carried out.
The random material required for the Diffie-Hellman exchange is generated by using the least significant bit from the microphone signal (not during calls of course), clock skew, and additional sources of entropy, and enhancing this entropy with the Fortuna algorithm. This scheme ensures that each key exchange is performed with a completely new and truly random key. For CryptoPhone calls a new key exchange is run for every call. For SMS the result of an initial key exchange is stored in the secure storage on the phone and used by means of a hash-chain.
The crypto block diagram is shown below:
CryptoPhone mobile phones run on top of a heavily modified and stripped-down Android OS. Android OS provides an affordable and well-researched platform that offers ample performance for the speech encoding and crypto functions. Android OS based system was chosen as the first CryptoPhone platform because it was the only sufficiently fast device allowed us to do software integrity protection in ROM and the stripping of unnecessary functions.
We are aware that there are risks associated with using any Android OS platform and we have taken a number of extensive measures to mitigate these risks as best as we could. We removed applications, communication stacks and system parts that are unnecessary for the CryptoPhone’s operation and which may cause potential security problems. Since we introduced our operating system hardening in 2008, for every attack that was published against Android since then we could show that we had already identified the threat and disabled the affected components years before in CryptoPhones. While this is no guarantee for the future, we have at least a provable continuous track record in respect to systematically securing mobile devices, which is much more than our competition has to show.
Most important for you as a user is that you should not install third party software on the CryptoPhone to prevent software based attacks on the firmware integrity. Protection against trojaned software that is intentionally installed by the user is nearly impossible, so it is your responsibility as a user to prevent that risk by not installing untrusted software on your device. The CryptoPhone firmware update mechanism is cryptographically secured.
The diagram below provides a schematic overview of the software architecture of GSMK CryptoPhones for your reference: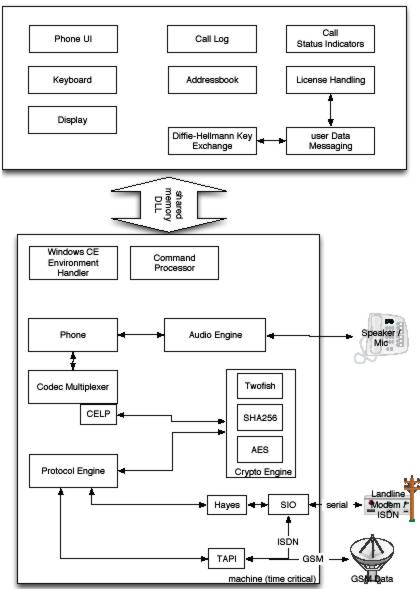
CryptoPhone Source Code
All GSMK CryptoPhone products come with their full source code published for review and to ensure provable security.
The ‘source code’ is the blueprint of how each CryptoPhone operates, and computer programmers can read this code. Cryptography/security is a fine art, and one simple error can introduce a serious flaw into the product. Customers of communication security devices have always had to fear not only programming errors, but also so-called “back doors”. Such a back door would allow certain people to listen into encrypted calls at any time, for instance by revealing (part of) the cryptographic key during the call.
Introducing a back door into a crypto system does not even require active cooperation of the manufacturer of the equipment. All it takes is one bribed programmer to compromise an entire product.
We prevent this by allowing anyone to review our source code. And even if you do not understand the source code yourself, you may find some comfort in knowing that there is a large academic community that likes a challenge, and will try to tackle our product. So any back door or programming error can (and will!) be found by eager students or security experts. Of course we tried our very best to write the code as well as we know how to. On top of this we have asked some of the world’s leading security consultants to look at critical parts of it. The conclusions of these ongoing evaluations are publicly accessible. So in theory you would not need to trust us at all, because you could verify everything yourself. This public review process is also the only reliable method for us to make sure that we are the only ones paying our developers ;-).
We can only assume that other vendors have something to hide. They might be afraid of competition and want to protect so called “trade secrets”. The nice thing about our products is that we have no (trade) secrets, and invite everyone to make interoperable products based on the published protocol. We believe in standards that are open for anybody to join – as long as they go and implement their own product and do not steal from our published source.
Some manufacturers of cryptographic equipment that are also currently in the business of selling secure mobile phones, have a track record of hidden cooperation with intelligence agencies and interested private parties. Some of them are not even using publicly scrutinized and standardized crypto algorithms (like Diffie-Hellman, SHA256, AES256 and Twofish that we use), but “proprietary” encryption methods that are not available for public evaluation. Several “proprietary” crypto-algorithms that were not subject to public review have been shown to be easily breakable in the past, like the COMP128 algorithm that is in use in many GSM networks for authentication, so the “proprietary crypto” approach has to be regarded as very risky. GSMK CryptoPhones contain only algorithms that are published, well known and thoroughly reviewed by the academic cryptography community.
We take a number of steps to ensure that you really get the correct firmware. The source code repository for all CryptoPhones is held on a computer that only our trusted developers can make changes to, and that is secured against physical access. After the security review by outside experts, but before each version of the firmware is released and used in the production of CryptoPhones, the source is compiled by a number of security experts who then publish the secure cryptographic SHA256-hash of the binary and of the source it is compiled from.
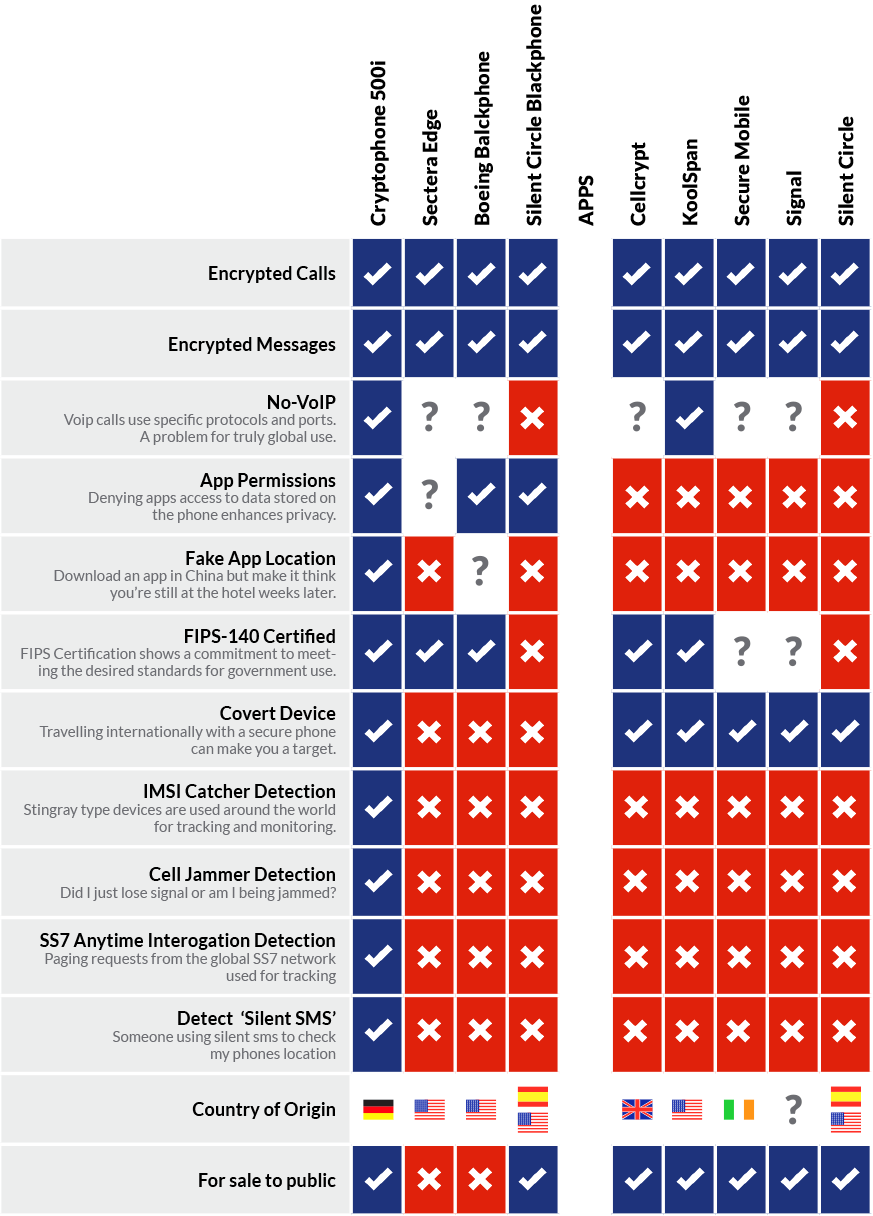
CryptoPhone Comparison
There’s more to being “secure” than just saying you are.